CKB's Stash
NASA 2021 Homework 1 Notes
本次的作業主題為網路封包分析工具,以及Shell script。我主要用Wireshark來做這題,因為我太廢不會用tcp dump,Shell script的部分時間有點趕沒寫DFS的部分,然後前面的一些地方也可能有錯Q_Q
- 題目: https://github.com/ChenKB91/nasa-2021-csie/blob/main/hw1/b09902011.pdf
- 官方解答: https://hackmd.io/@uqzWTXyyTk6IYTBwcPwnoA/HJka804N_
NA
野生的密碼難道會在網路上赤裸地奔馳著?
本題提供了兩個版本的網站,一個用http一個用https,網站上有個輸入密碼的欄位,http的版本可以直接用wireshark攔截到。
-
We can simply filter by http and get this, since http don’t do encryption:
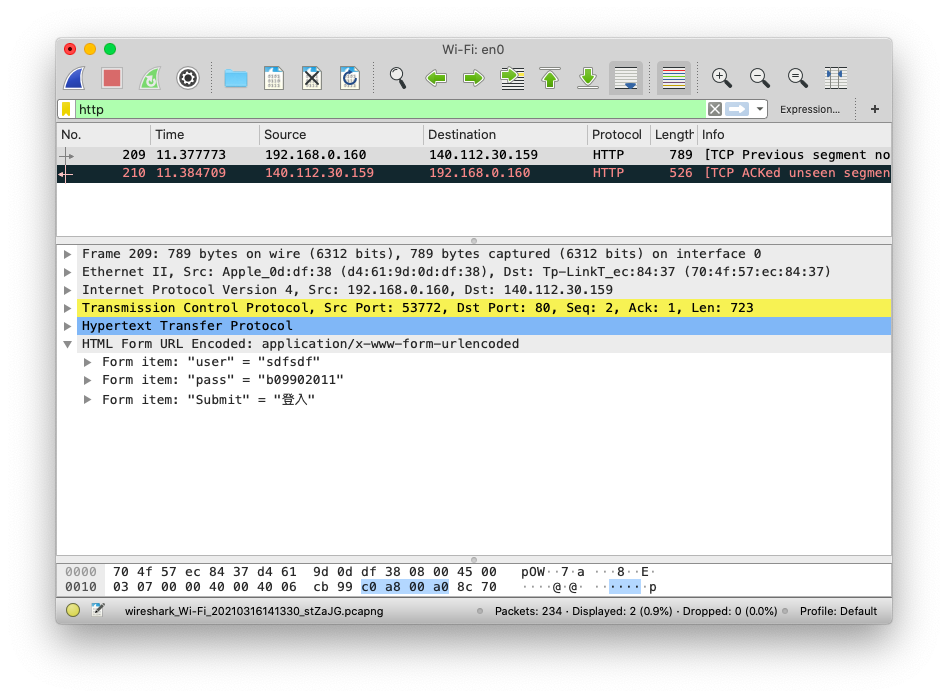
-
This version uses https, which encrypts requests & responses, so we can’t get our password from Wireshark.
好玩遊戲也有暗潮洶湧的一面
本題提供了一個Ubuntu虛擬機,打開之後可以執行./client-linux來玩一個乒乓球遊戲,虛擬機也載了Wireshark,可以直接拿來用。
-
We can use “Conversations > Follow Stream” to inspect these conversations while we play:
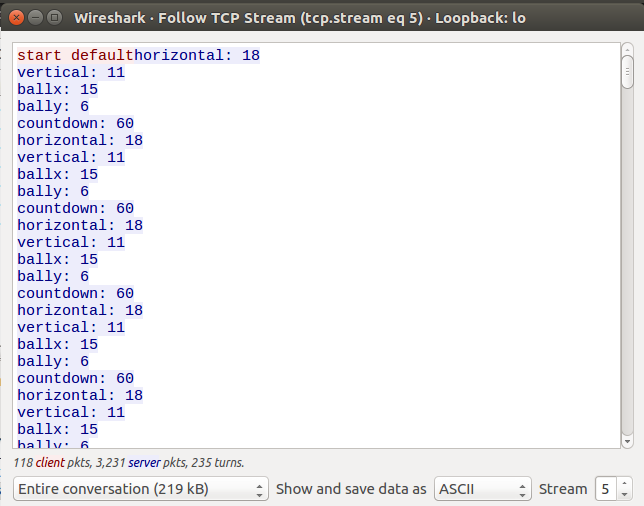
We can also view only data sent by our side:
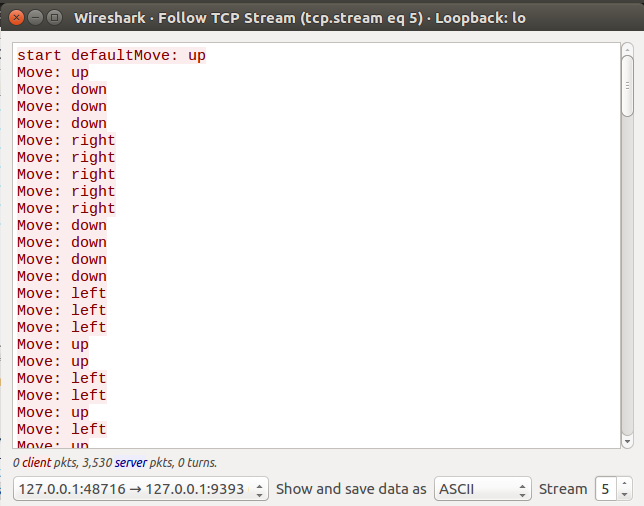
So basically, the game server sent us the time, the ball and the pad’s location, and the client send directions when we press move.
-
If we pay attention to the conversations page, we can notice at some point there’s another conversation happening on port 9394:
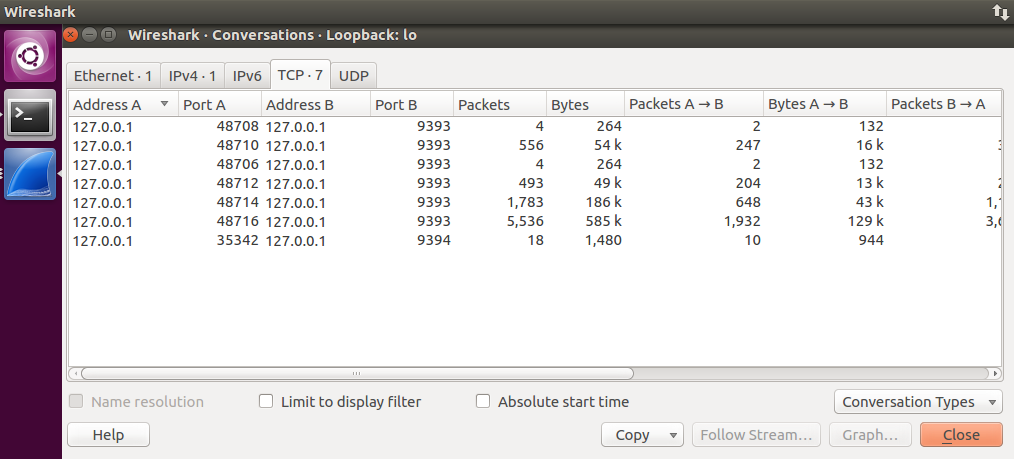
And when we look into it we’ll discover this:
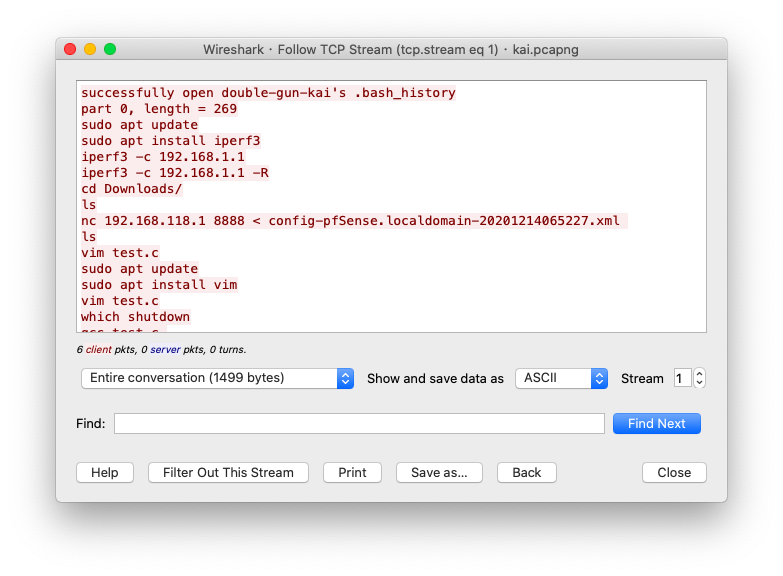
So we know the game steals our .bash_history.
-
We repeat the above steps with the pcap:
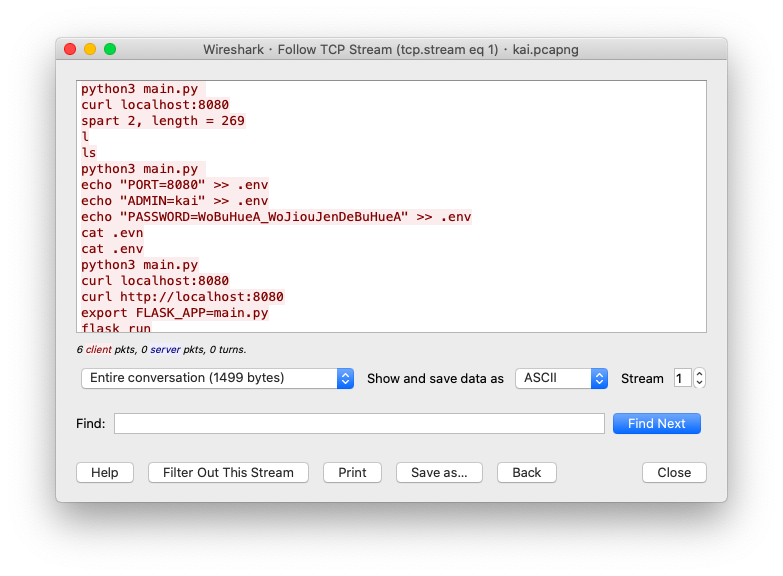
PASSWORD=WoBuHueA_WoJiouJenDeBuHueA -
I wrote a quick python program to communicate with the server, since we already know the port and the format:
import socket host = '127.0.0.1' port = 9393 with socket.socket(socket.AF_INET,socket.SOCK_STREAM) as s: s.connect((host,port)) print('connected') s.sendall(b'start fast') while True: data = s.recv(1024).decode('ascii') if 'hori' not in data: # Stop when recieving anything not game data print(data) break else: data=data.split('\n') # Make sure it don't explode when server asks for secret plus = 0 if 'secret' in data[0]: plus = 1 x=int(data[0+plus].split(' ')[-1]) y=int(data[1+plus].split(' ')[-1]) bx=int(data[2+plus].split(' ')[-1]) by=int(data[3+plus].split(' ')[-1]) t=int(data[4+plus].split(' ')[-1]) if x<bx: s.sendall(b'Move: right');print('r') elif x>bx: s.sendall(b'Move: left');print('l') elif y>by: s.sendall(b'Move: up');print('u') elif y<by: s.sendall(b'Move: down');print('d')Got the flag:
HW1{d0_y0u_knovv_wH0_KaienLin_1s?}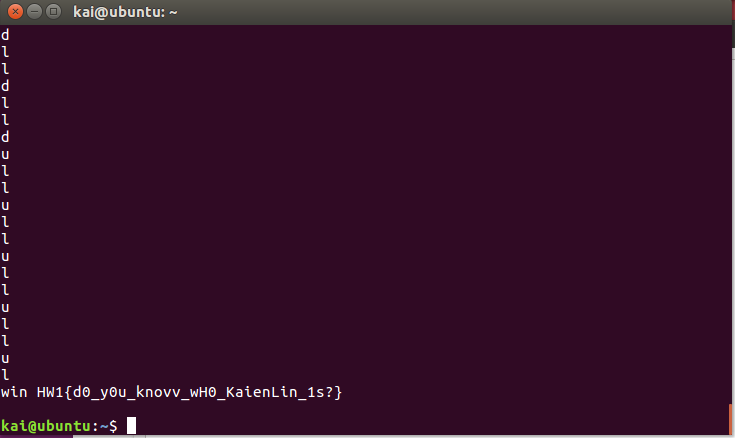
-
I’m too lazy to modify the program to play with 2 balls… Using
netstat -tulpnwe can find the server running on port 9393, then copy it. We already know the flag format, so…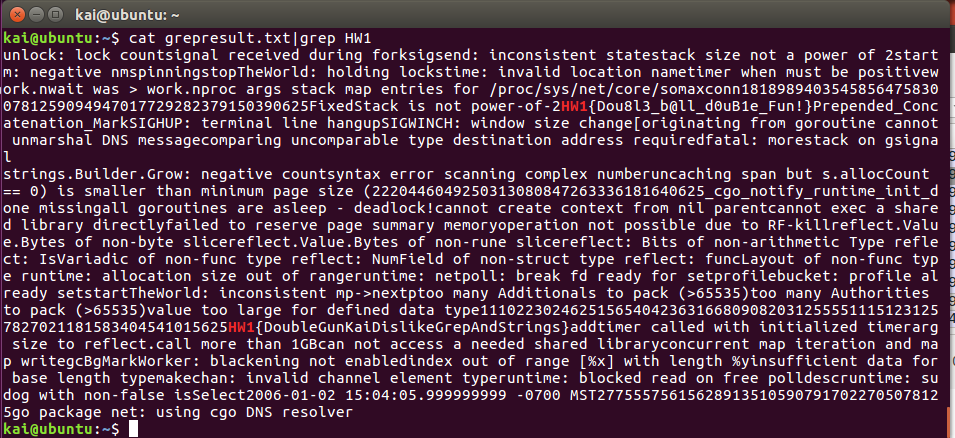
Flag:
HW1{Dou8l3_b@ll_d0uB1e_Fun!}
這麼多的網路協定要是能全部都認識的話該有多好
-
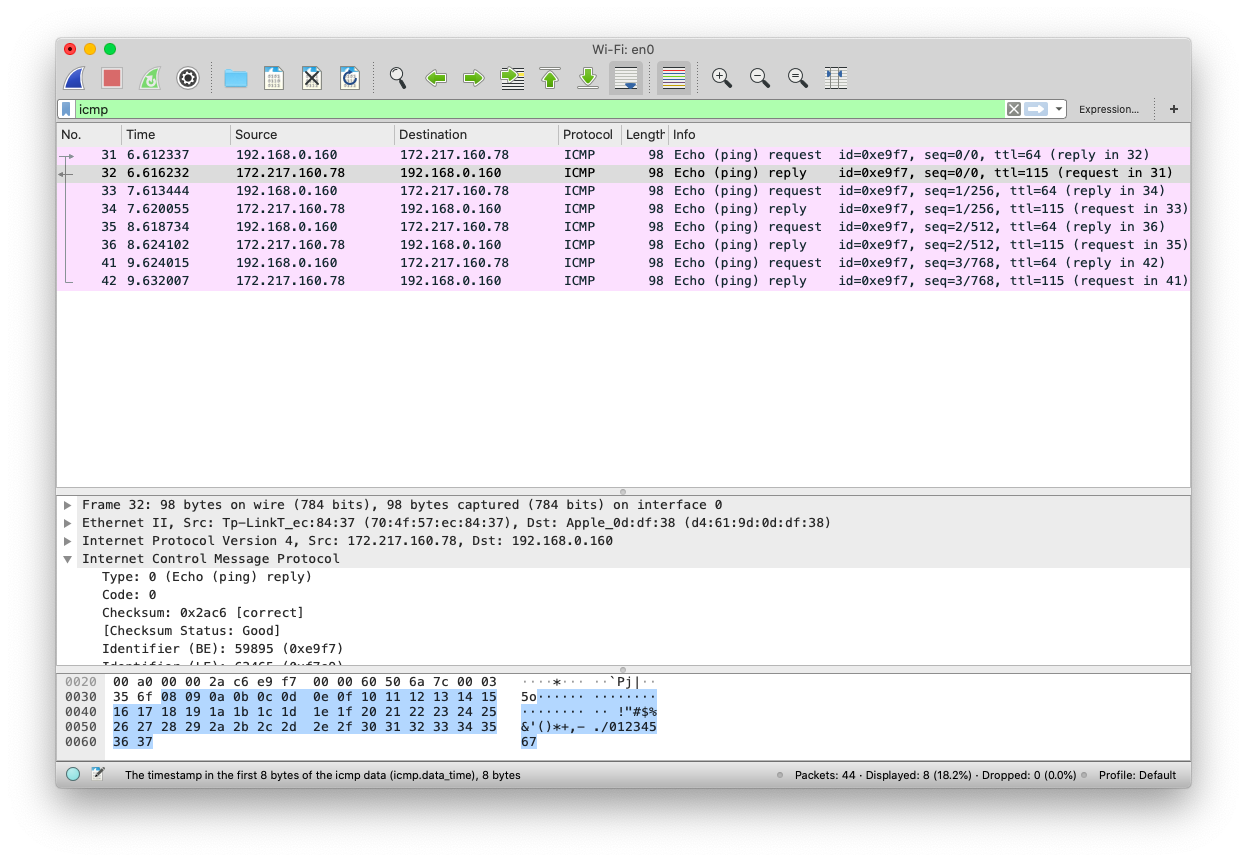
ICMP, or the Internet Control Message Protocol is used to send error messages and other informations, for figuring out networking issues. It is built on the Network Layer.
-
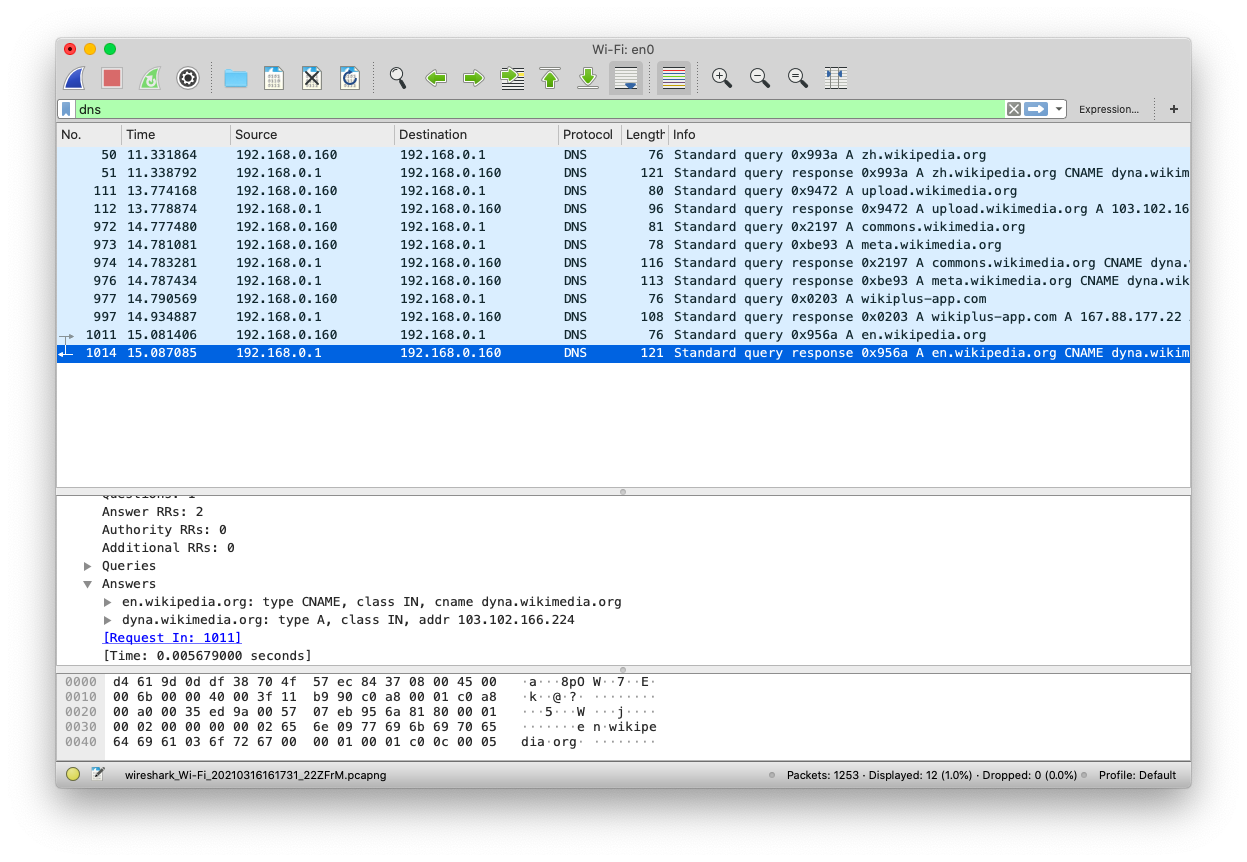
DNS protocol is used to communicate with DNS servers, and figure out a domain’s IP address. It is built on the Application Layer.
-
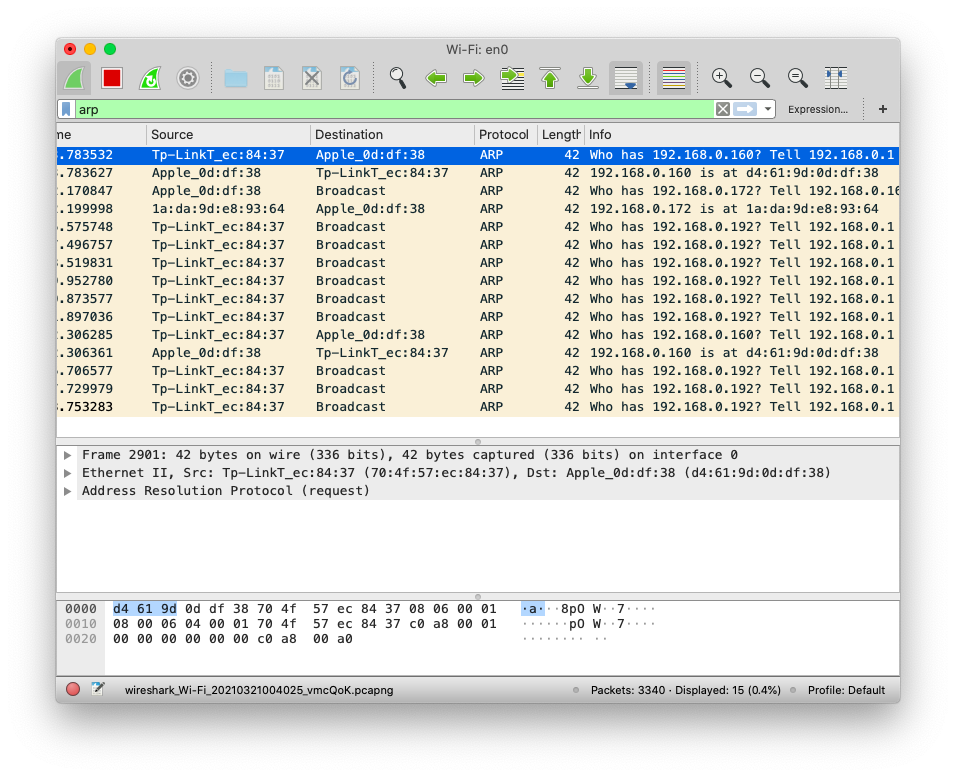
The ARP protocol, or the Address Resolution Protocol, is used to in a local network to communicate MAC addresses. It is built on the Data Link Layer.
-
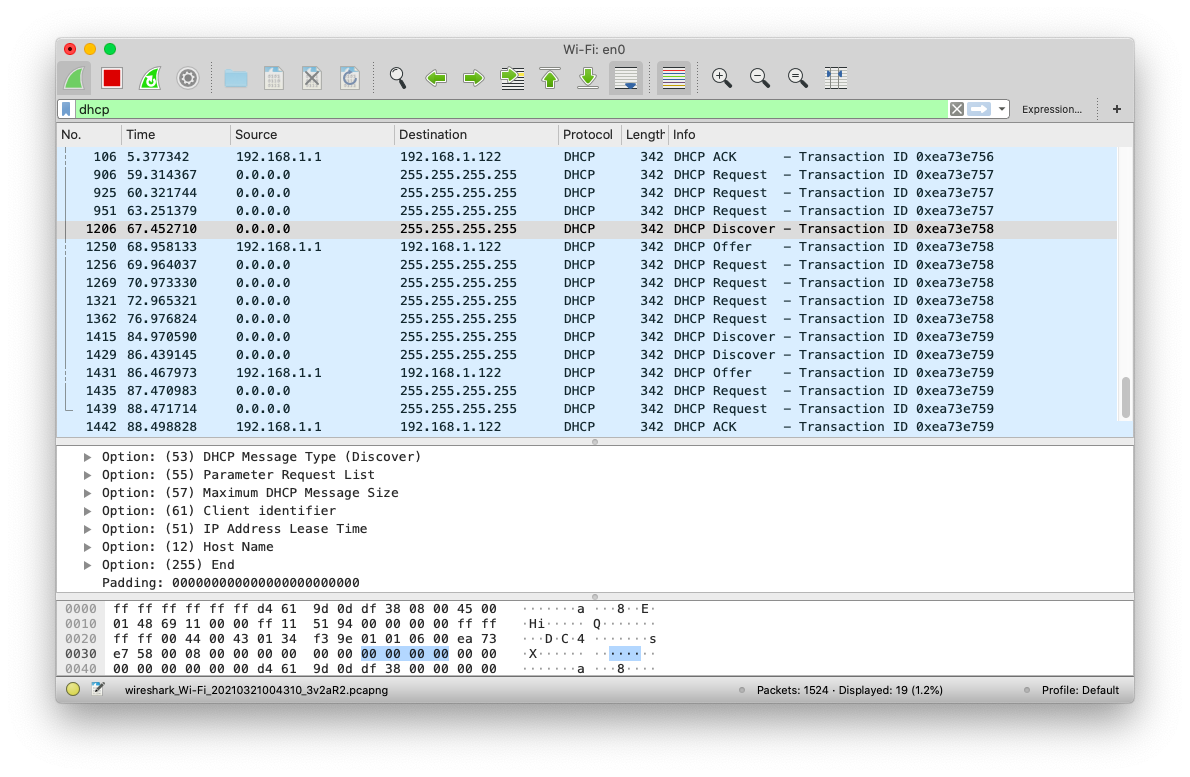
DHCP protocol, or Dynaic Host Configuration Protocol, is used to communicate with DHCP servers when connecting to it. It handles the process of getting an IP address inside a network.
SA
我寫的Shell script:
- P1: https://github.com/ChenKB91/nasa-2021-csie/blob/main/hw1/p1.sh
- P2: https://github.com/ChenKB91/nasa-2021-csie/blob/main/hw1/p2.sh
- P3: https://github.com/ChenKB91/nasa-2021-csie/blob/main/hw1/p3.sh